记录计算机网络原理,流量分析相关。
使用tshark过滤HTTPS流量
1 | foreach($f in gci pcaps *pcap) |
- -r:表示加载本地文件
- -Y:表示过滤条件,这里过滤条件是443端口
- -F:表示存储的格式,这里指定pcap,如果指定为pcapng则SplitCap不能加载
- -w:表示存储文件
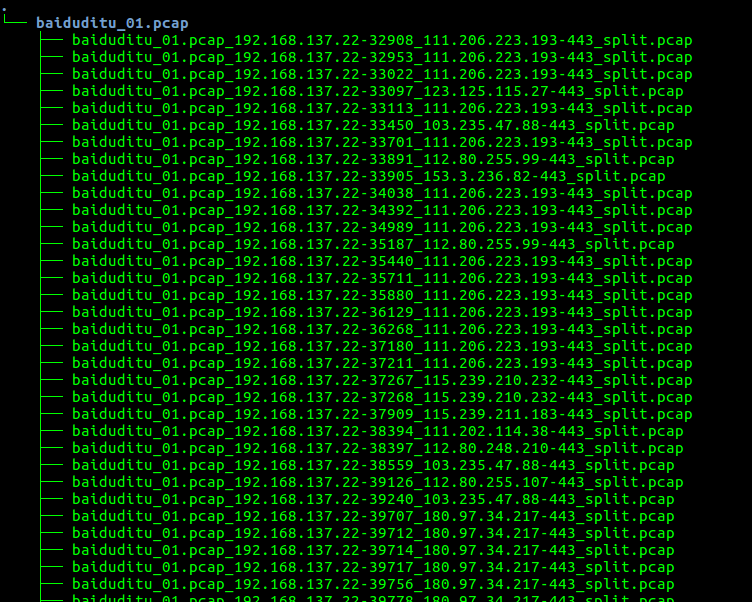
使用SplitCap切分流
1 | foreach($f in gci 1_Pcap *.pcap) |
- 等待被处理的文件
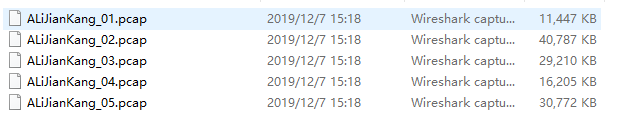
- 处理之后的文件
nslookup批量处理域名
1 |
|
以上,$1是第一个参数,就是要打开的域名文件,$2是跟在命令后的第二个参数,是需要保存结果的文件。^Name -A1表示:找到以Name开头的行,-A1表示显示下一行,grep的具体使用如下:
1 | 使用方式:grep [OPTIONS] PATTERN [FILE...] |
包分析(packet to flow)
工具安装
1 | # ==========软件依赖============= |
pcap按照TCP flow切分(Scapy+Python)
主要功能与Windows下的SplitCap类似,使用Python2.7基于Scapy编写的脚本,代码如下:
1 | #!/usr/bin/env python |
输出:建一个与当前pcap文件名相同的文件夹,如,当前python split-pcap.py scapy-split-pcap.png保存如下: